
Short for Distributed Denial of Service, DDoS attacks refer to malicious bombardments of a site’s or app’s servers with massive amounts of fake traffic or page requests.
The targeted system can’t handle that much traffic and eventually buckles under pressure, becoming unusable to end users.
Such an outcome can be particularly disastrous for site owners and businesses like news publications and online stores that rely on continuous uptime to generate income.
Ergo, DDoS protection is paramount as it can safeguard against damage to the bottom line and reputation.
-
Navigate This Article:
Understanding DDoS Attacks
All it takes are two devices (say, your smartphone and laptop) programmed to form a DDoS network and send fake traffic to a server.
Because DDoS attacks are relatively easy and inexpensive to create, 2023 saw a new all-time high — more than double year-over-year in the fourth quarter.
Depending on their size (but also the existing level of protection), downtime can last for hours or days.
Historically speaking, DDoS attacks have always been a major pain because the victims are usually those with inadequate IT security. It’s important to understand that these are targeted attacks, meaning that cybercriminals deliberately select whom to attack.
How DDoS Attacks Work
Threat actors generate huge volumes of data packets or connection requests via botnets, large groups of hijacked computers and devices. These work in unison to overwhelm the target’s infrastructure with more internet traffic than it’s equipped to deal with.
An attacker will implant malware or exploit an unpatched vulnerability on someone’s server to obtain access. Unfortunately, many servers lack sufficient security, which is why hackers can fairly quickly and easily assemble networks of computers and IoT devices under their control.
Once they have enough machines, they issue a command to the botnet to access the target system. Since a server can’t process that many access requests simultaneously, service is interrupted.
Common Types of DDoS Attacks
Though the core principle is the same (to overwhelm a target), DDoS attacks come in various types depending on the point of the internet connection they strike.
1. Volumetric: Feature bots send large amounts of data via some form of DNS amplification, expecting a server response. By redirecting DNS requests to the spoofed (victim’s) IP address, the attacker can have the DNS servers respond to the victim.
The resulting response becomes too long, eating through available bandwidth at full tilt and leading to stoppage.
2. Protocol: Focusing on weaknesses in the procedures that govern online communications, protocol attacks seek to swamp a target by sending connection requests from different spoofed IP addresses.
They exploit the TCP handshake as the target machine responds to each connection request and then waits for confirmation that never happens. The incomplete handshakes eventually build up and fully exhaust the target server’s capabilities.
3. Application layer attacks: Often labeled as layer 7 attacks (in regards to the final layer of the OSI model), these try to drain the resources of a website, web app, or service by generating countless HTTP requests.
The target server’s bandwidth is effectively eaten up as for each request, the server has to load several files and run database queries. It does so because legitimate and malicious HTTP requests are tough to distinguish, ultimately generating a workload it can’t handle.
This makes application layer attacks the most frequent form of DDoS attacks.
It’s worth noting that these blitzes can be aimed at any publicly reachable internet endpoint. A cybercriminal can use more than one vector attack or cycle, often as a means to avoid countermeasures performed by the target.
Motivations Behind DDoS Attacks
Some of the possible reasons behind these efforts to paralyze communications and services include:
- Extortion: In most cases, inflicting punitive damage on the victim behind this illegal activity. Usually, attackers demand a ransom, threatening with long downtime or exposing specific data if payment isn’t received.
- Competitive advantage: Resembling a movie-like villain, it’s not uncommon for businesses to engage in DDoS attacks to disrupt the operation of a competitor and thus gain an advantage in their respective market.
- Politics: Politically motivated incidents are a part of the growing DDoS attack trend, especially when election time is near. The goal is to interrupt campaign sites, censor or suppress voter information or registration websites, or any other publicly accessible websites.
- Activism: Attacks driven by ideological beliefs, perpetrated by hacktivist groups protesting against certain policies or organizations they consider unethical and/or destructive. This is their way of showing displeasure with some actions, thus drawing attention to their cause.
- Others: State-sponsored high-level cyber warfare, espionage, cyberbullying, retaliation against a person or company — there is no shortage of motivations.
Basically, anyone with any financial, ideological, or ulterior motive can deal damage by initiating a DDoS attack against a target.
Heck, some hackers are simply testing or proving their capabilities just for the “fun” of it or sheer boredom. It may not always make sense, which is the scary part if you ask me.
Real-World Examples of Significant DDoS Attacks
All DDoS threat actors have one thing in common: They don’t discriminate. This “anything goes” mantra means they threaten a wide array of victims with monetary and productivity losses. Here are a few real-world incidents notable for their scale and overall impact.
Google, August 2023
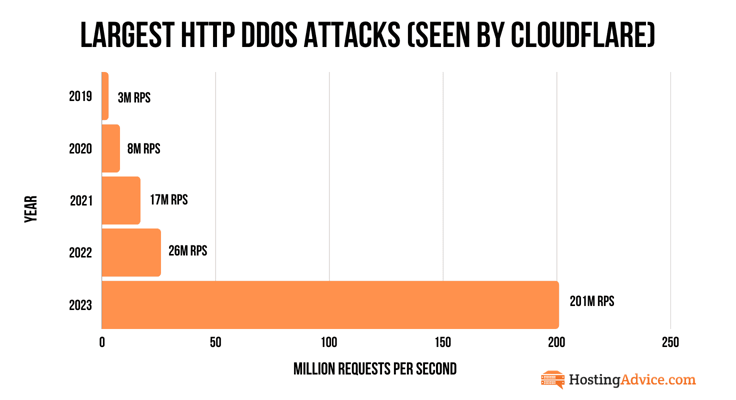
Even tech giants such as Google are grappling with DDoS attacks. It intercepted what is now known as the largest DDoS attack in history, peaking at a staggering 398 million requests per second (rps). To get an idea of how big this was, here’s what Google wrote:
“For a sense of scale, this two-minute attack generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023.”
This act of cyber aggression also revealed a disturbing trend of DDoS attacks rapidly evolving in size and sophistication, as the previously largest DDoS attack ever recorded by Google peaked at “mere” 46 million rps.
VoIP.ms, September 2021
Canadian VoIP provider VoIP.ms faced a DDoS attack on its DNS name servers. The attackers demanded a $4.2 million ransom to stop, controlling the company’s site and severely damaging its telephony services.
What’s notable about this incident is that it took almost two weeks for VoIP.ms to update its infrastructure and restore service to customers.
Google, October 2020
Originating from three Chinese IP addresses, this attack lasted for half a year (!) and generated a traffic load of 2.5 terabits per second at its peak.
While not the largest attack in terms of bandwidth, it’s mention-worthy because of its tenacity and attack surface of about 180,000 exposed servers.
Strategies for DDoS Protection
The above-mentioned examples paint a clear picture of the dynamic nature that DDoS cyber threats represent. So, staying afloat requires both constant vigilance and a proactive approach to security.
Network-Level Protection: Filtering and Traffic Scrubbing Techniques
Every person on a network generates traffic with distinct patterns at different layers, creating a footprint that differs from spoofed traffic.
By monitoring and analyzing these patterns, DDoS protection services can reliably tell genuine users from potential attackers, scrub and filter out malicious traffic, and forward the clean traffic to the server.
This works thanks to the following techniques:
1. Rate limiting and traffic shaping: If configured the right way, rate limiting can filter requests without negatively affecting actual users.
It achieves this by restricting the number of requests a server will accept over a specific time frame, generally by setting up rate limits on network devices.
While it provides defense against multiple automated requests and web scrapers intent on stealing data, it won’t be enough to deal with a complex DDoS attack.
Hence, you should complement it with other measures, such as traffic shaping, which routes all incoming traffic through a buffer.
In essence, it collects traffic peaks in the buffer and sends them when the server is ready/able to process them. In deferring excess traffic rather than discarding it, available bandwidth is more efficiently used.
2. IP blacklisting and whitelisting: Based on denying or allowing requests from specific IP addresses by identifying regular from attacking ones.
You can block access based on an IP address directly or by a specific characteristic such as country/region or reputation known to the anti-DDoS solution you’re using.
Databases of IP addresses known to be sending spam, hosting malicious content, or hijacking IP space can be found online, and some services gather this information in specialized libraries.
As is the case with rate limiting, IP blacklisting and whitelisting aren’t a foolproof method of protection as they only partially solve the issue at hand.
For instance, an attacker can change their IP and bypass the block, then carry on with the attack. Plus, blocking one infected IP address can affect hundreds or thousands of legitimate users, as blacklisting only pins down the IP ranges, not an individual.
It’s always prudent to remember that dependable protection against DDoS attacks relies on a comprehensive approach. That way, you can cover all possible network-level weaknesses that hackers may exploit.
Anycast and DNS-Based Solutions
For the uninitiated, Anycast is a network addressing and routing methodology frequently used by CDNs in which servers share a single IP address in a variety of locations.
In the context of a DDoS attack, Anycast distributes the remaining attack traffic across data centers, normally to the nearest ones with the capacity to process the traffic efficiently.
This selective routing increases the receiving network’s surface area and spreads the attack’s impact. As a result, the traffic is scattered, preventing any one location from becoming overwhelmed.
In conjunction, DNS-based solutions work on the same distributed basis, where each server node communicates with other instances on other servers across data centers.
They share threat intelligence to supply extensive protection within each data center, facilitating immediate detection and mitigation.
Application-Level Protection: Mitigating Layer 7 Attacks Targeting Web Applications
Because layer 7 DDoS attacks employ HTTP traffic to flood networks and servers, they are more difficult to handle and more detrimental. The good news is that there are ways to reduce their effect.
1. Web Application Firewalls (WAF): Protects by filtering the HTTP traffic to and from the web application.
Custom rules and policies (which can be rather complex and cover every HTTP request parameter and field) can detect abnormal surges in traffic before they can “land” on a server and impede a layer 7 attack.
For example, instituting rate-limiting rules allows WAF to block clients from receiving an irregular number of requests to your app, server, or website.
Risking sounding like a parrot, I must once again point out that WAF isn’t meant to be the primary defense tool in your anti-DDoS arsenal.
It can’t offer suitable shelter against high-load and multi-vector attacks, so you should use it as a supplement to your greater security package.
2. Intrusion detection and prevention systems (IDPS): These passively monitor a network and continually scan for potential threats to block suspicious or malicious behavior once it is flagged.
Depending on where it is deployed, an IDPS system can react quickly due to its access to network or host packets.
Once in place, it uses several techniques to identify threats. A signature-based threat detection identifies known attack signatures (unique patterns or identifiers) by matching current activity with historical data.
On the other hand, anomaly-based threat detection matches a random selection of network activity against a predefined benchmark.
A protocol-based variant works similarly, employing predetermined standards of each protocol and blocking any activity that deviates from those standards.
Layer 7 attacks represent a special challenge since they necessitate deeper-than-usual insights into application performance and behavior to separate legitimate requests from malicious ones.
So, preventing these assaults should be a top priority if your business revenue greatly relies on your continuous online presence.
API Protection and Bot Management Solutions
These map out the API attack surface via an automated machine learning algorithm that discovers vulnerable points. It then forms tailored security policies to detect and block API-focused attacks as they take place.
With AI in charge, the system can distinguish whether the request came from a human or a bot in a couple of milliseconds, all the while evaluating behavior at specific endpoints — supplying threat analytics with real-time reports.
Slowly but surely, SaaS vendors are moving toward a single coherent system where bot traffic management and API security integrate with traditional WAF functionality and DDoS protection.
Such system architecture provides encompassing security, meaning you also get protection from fake account creation, card fraud, account takeover, and more.
Cloud-Based DDoS Protection Services
The biggest advantage of a cloud-based DDoS protection service is its scalability to shield any kind of infrastructure. Regardless of where it’s going, the harmful traffic will always pass through the same mitigation network, where it will be scrubbed. There are a few options here:
CDNs With DDoS Mitigation Capabilities
The very design of a CDN is conducive to protecting against DDoS attacks as it redistributes network traffic evenly across multiple servers to ensure optimal use of resources.
Plus, its on-demand scalability is excellent for handling sudden spikes in traffic. This feature allows easy scaling to meet increased demand and deliver an uninterrupted user experience.
However, a CDN is still primarily a distribution service and, as such, is only part of the solution. When paired with DDoS mitigation features and properly configured, it creates a hard-to-penetrate buffer between a web server and end users.
Acting as a reverse cloud-based proxy, it shelters assets without calling for human interaction against network and transport layer DDoS attacks.
On the application layer, CDNs with DDoS mitigation capabilities are often combined with custom WAF rules to shut out HTTP-specific attacks.
Dedicated DDoS Protection Platforms Offered by Major Cloud Service Providers:
Major cloud service providers offer a potent mix of automatic machine learning algorithms, manual traffic scrubbing, and custom filters that cover a variety of purposes.

Most cloud providers offering these platforms use the Border Gateway Protocol (BGP) or DNS to divert traffic to their mitigation centers. Once it’s diverted, the mitigation service scrubs the malicious attack traffic and returns the clean traffic to the customer.
Thanks to anomaly detection, it’s possible to uncover unusual patterns in network traffic and hone in on potential dangers early, thus allowing for speedy preventive action.
Since these are cloud-based solutions, they can seamlessly scale to adapt to shifting traffic levels, especially during attack peaks, to provide steadfast performance.
Hybrid Approaches Combining On-Premises and Cloud-Based Protection
A hybrid DDoS defense includes stateless deep packet inspection (a type of firewall that filters network traffic based only on the information in individual packets) at the network edge and cloud protection to stop large volumetric attacks.

This way, you get most of the advantages of cloud security and on-premises management while minimizing their cons.
Here’s what I mean by that: On one side, you can catch and stave off network exhaustion and application layer attacks, while on the other, you put an end to mitigation errors that cause collateral damage to genuine users and traffic.
Since on-premises protection mitigates most DDoS attacks locally and uses cloud DDoS mitigation for volumetric attacks, you benefit from cloud scrubbing while maintaining the operator control of an on-premise solution.
With things going as they are, businesses will become even more dependent on cloud technology for mission-critical processes.
Therefore, it’s safe to say that cloud-based DDoS protection platforms will be paramount in ensuring that all kinds of DDoS attacks are caught on time and dealt with promptly.
Implementing DDoS Protection Measures
Though DDoS techniques continue to become more advanced and complicated, there are fundamental steps you can — and should — take to prepare the ground for an effective DDoS protection and mitigation strategy.
Assessing Risk and Identifying Critical Assets for Protection
Fancy pulling off a DDoS attack on yourself? The idea is to run massive network attacks and stress the system to check the status of your protection framework. For that, you’ll require an IP stresser/booter tool (100% legal, in case you were wondering).
It runs a simulated DDoS attack on the targeted system to determine whether the existing resources are sufficient to handle the extra load. Alternatively, third-party companies offer simulated deep multi-vector network, protocol, and application-layer attacks.
After you’re done, make a list of systems that are the weakest links in the chain. In the event you get hit, it will help you possibly isolate and save systems that haven’t been affected.
Choosing the Right DDoS Protection Solution
For starters, look for a vendor that implements a multi-layered security approach, including network, application, and data protection.
The platform of your choosing should be proactive. This means real-time scrutiny of network traffic for suspicious activity, timely alerts, detailed reports, and instant mitigation to reduce the impact of an ongoing attack before it develops into a real mess.
Ideally, they should use behavioral learning algorithms to establish legitimate traffic patterns. Considering that attack vectors and sizes keep changing for the worse, a good DDoS protection provider must repeatedly invest in its defense capacity and stay ahead of the latest trends.
Integration with Existing Infrastructure
Once you settle your eyes and money on a provider, it’s important to give thought to the deployment model:
- On-premise appliance: Hardware is located in your data center.
- On-demand cloud service: Only activated upon detection of a DDoS attack.
- Always-on cloud service: 24/7 protection against DDoS attempts.
- Hybrid protection: Combines hardware components and cloud-based service to get the best of both worlds.
Several factors will influence your final decision. For instance, your company’s threat profile.
If you’re regularly bombarded with nonvolumetric DDoS attacks, a premise-based solution might be the way to go. If large-scale volumetric attacks are pounding your assets, then a cloud-based or hybrid solution might be a better fit.
Then, you need to factor in latency sensitivity, your data center plans, how much control you want to retain, budgetary restrictions, and so on.
You must decide which deployment makes the most sense for you. Each has pros and cons, so make sure you drill down into details before you decide.
Training and Awareness
It’s imperative to train your security and network team on DDoS prevention and response protocols.
They must know how to spot potential threats, which component will stop which attack vectors, what to do in different scenarios, and how to remedy the situation (divert traffic if needed) quickly.
Essentially, you’re building a human firewall that will be the first layer of defense in avoiding an emergency scenario.
When everyone is clear on the game plan, the burden on incident responders is reduced. Recognizing early warning signs and adequately reacting to them can significantly contribute to hasty threat identification and mitigation.
Best Practices for DDoS Resilience
Besides setting up protection measures, you can do more to react in an orderly and timely manner that keeps business as usual. Think of the following as tenets to live/resist DDoS attacks.
Proactive Monitoring and Threat Intelligence
The key is to stay ahead of potential DDoS threats by recognizing distress signs before they turn into full-scale assaults.

Proactive monitoring aids in establishing a benchmark of normal activity, one that includes average and high-traffic days. Doing so helps in understanding what is and isn’t regular behavior.
Throw in a real-time analysis and you can detect unusual activity patterns (such as traffic spikes) that could signal trouble is brewing.
One step that is equally vital here is maintaining a current threat intelligence database. Timely updates will not only address newly discovered vulnerabilities and exploits but also remit as much risk as possible from the get-go.
Most updates are automated and require a few clicks at the most, so there’s no real reason why any of this should fall by the wayside.
Incident Response Planning
Remember the simulated self-sabotage I suggested? One underrated benefit is that it also simulates a demo response you can use as a starting point to create your incident response plan for DDoS emergencies.

Start by forming a response team with clearly outlined roles and responsibilities for each member.
Then, work on a checklist that precisely defines the response procedures, mandatory tools, and resources that will be needed during a DDoS attack. You should also include steps to mitigate and recover from the attack.
Add a chain of communications designating who needs to know what and when. By this, I mean your clientele, protection service provider, and any other third-party vendors. They will need to be informed about what’s happening so that they can each respond accordingly.
When the plan is ready, rehearse it until every member knows what to do with one eye closed.
Collaboration and Information Sharing
The global DDoS threat landscape occasionally ups the ante, so collaboration between all stakeholders will be crucial to adapting to and meeting these new realities.

So, reach out to specialized DDoS protection service providers for additional expertise and resources to augment in-house capabilities.
Contact those on the front lines of the battle to get actionable advice based on their experience. Engage with industry peers and security communities for more data and insights into the identification and mitigation of new attacks.
Every bit of information will help to lessen impacts on systems and operations.
Continuous Improvement
In this field, complacency will be your downfall. There is no guarantee that what works right now will work in the near future.

You want to periodically reassess and reinforce your DDoS protection strategies based on new findings.
This entails regularly identifying and patching root causes and vulnerabilities, more so if you’ve been a victim.
Becoming familiar with the weaknesses that threat actors target in the latest DDoS attacks can also reveal the problematic areas to address while bolstering your defenses at network and application levels.
From time to time, conduct penetration testing and incident response drills to verify the efficacy of your protection solution.
Regulatory and Compliance Considerations
Amidst all the trouble a DDoS attack brings, you don’t need legal wranglings to hang over your head. Yet, associated risks extend well into that territory.
Legal and Regulatory Frameworks
The style of DDoS attacks and the techniques used tend to make it hard to identify who is responsible, which means there is a chance it could be you.
Considering a victim of a DDoS attack can sue the responsible party, you don’t want to risk being sued by a customer who suffered damage as a result.

Thus, have your legal and regulatory personnel review the internal DDoS policies and align them with external requirements. This is especially important if you’re doing business abroad, as DDoS attack laws and regulations vary worldwide.
The Cybersecurity Framework DDoS Threat Mitigation Profile might help. It was created by the Cybersecurity Coalition to provide a detailed overview of legal and regulatory considerations for DDoS attacks, including relevant frameworks.
Compliance Requirements
In much the same way, DDoS attacks can trigger compliance issues depending on your industry and the data you handle.
Some industries like finance and healthcare have more stringent requirements regarding data security, which necessitates specific measures to mitigate DDoS risks (e.g., you need to comply with PCI DSS for online transactions).
The compliance team must determine if your company has implemented the correct policies to protect against DDoS attacks.
The first place they’ll have to look is your incident response plan to see if the set procedures (including reporting the attack to relevant authorities) align with relevant standards.
Data Protection and Privacy
Finally, your DDoS preparedness must consider data protection regulations and privacy standards like GDPR and CCPA that restrict how personal data is collected, stored, and used.
A successful DDoS attack that disrupts access to this data could be considered a breach, triggering reporting obligations to users and a whole lot more headaches.

Let’s take CCPA as an example. It grants Californians the right to know what data about them is collected and to request its deletion. So, you need to bear this in mind when crafting your DDoS mitigation data practices.
A good idea is to implement data minimization techniques (anonymizing or aggregating data as much as possible) and be transparent about your data collection practices.
Future Trends in DDoS Protection
While DDoS attacks will go on to grow in size, complexity, and sophistication, the good news is that the tech industry is beefing up its weapons cache to fight back.
Evolution of DDoS Attack Techniques and Trends
In 2023, DDoS attacks have become longer, more persistent, and increasingly advanced due to the constant growth in digital and cloud technology.
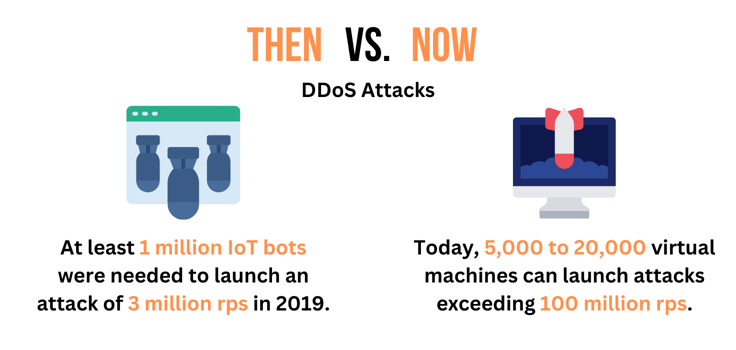
Here’s some perspective to see how bad the situation is. According to Cloudflare, it took at least a million IoT bots in 2019 to launch an attack that reached 3 million requests per second.
Today, you only need 5,000 to 20,000 virtual machines to launch attacks that easily exceed 100 million rps. And if that wasn’t enough, many attacks exceed the one terabit per second rate almost every week.
Generative AI plays a major role in enhancing scripts and executing more sophisticated attacks.
It assists in processing millions of independent service requests within seconds, overloading servers in the blink of an eye.
The deployed malware operates through variable AI models to mask its intention until it does its job, rendering standard defense protocols null and void. This has intensified the quantity of attacks, with no end in sight.
Advancements in DDoS Mitigation Technologies
On the other side, artificial intelligence is leading numerous mitigation efforts and setting next-gen protection standards. It can go through a huge amount of network traffic data in real time while simultaneously identifying cyber threats.
A major benefit of using AI in DDoS defense lies in its ability to adjust to changing threats instantly. Using advanced machine learning algorithms, AI-driven systems can achieve higher precision in differentiating between normal and malicious traffic.
As attackers alter their methods, these systems can rapidly update their response tactics to neutralize emerging threats efficiently.
By keeping tabs on online forums and hacker communities, analyzing threat intelligence feeds, and spotting signals of imminent attacks, AI can also predict potential DDoS attacks.
Anticipating such attacks means organizations can act in advance to strengthen their defenses. To top it all off, intelligent traffic filtering can automate mitigation efforts.
With advanced analysis techniques such as deep packet inspection (DPI), content filtering, and Quality of Service (QoS) policies, AI provides deeper visibility into network traffic and applies filtering decisions to maintain service availability.
Integration With Emerging Technologies
Although their introduction means new attack surfaces and challenges for DDoS protection, technologies like IoT, 5G, and edge computing also offer opportunities to forge a more layered and proactive defense.
For example, IoT can elevate threat intelligence and improve early warning by strategically placing devices known as honeypots. These are designed to mimic real systems, applications, or services and can be employed as decoys for attackers.
By enticing cybercriminals to interact with these devices, it’s possible to observe and analyze their tactics and techniques.
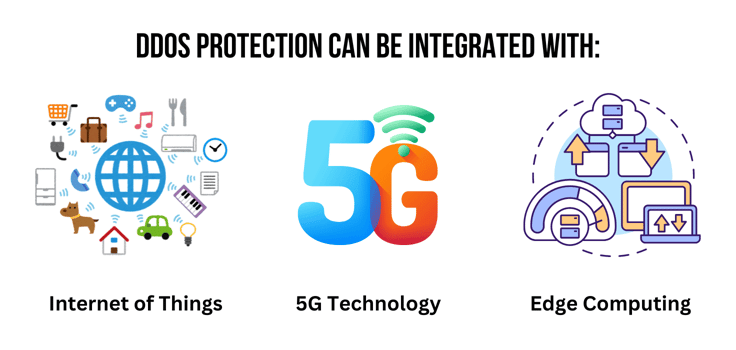
Then, 5G networks can be leveraged for network slicing, a technique that creates multiple virtual networks on top of a shared physical network. This segregation allows for targeted and localized mitigation strategies if a DDoS attack targets a specific slice.
Edge computing infrastructure can be applied directly to the application layer. Being closer to the source can accelerate the detection, filtering, and blocking, radically limiting the damaging impact.
These are just some of the examples of what can be done. With a little ingenuity and quality work, DDoS mitigation strategies can incorporate the latest tech to fight whatever new DDoS beast emerges.
Future Predictions
It’s safe to say there will be more sophistication and automation on both sides of the fight. We’ll likely see more IoT exploits as more of these devices become household items.
They lack strong security and hackers are taking advantage of that, so it’s reasonable to assume we’ll see a more concerted effort to plug weak points of entry and use them for learning purposes into how criminals operate.
In terms of specific technology, a more widespread use of multi-CDN strategies is a real possibility.
This would involve dispersing traffic among multiple CDNs and optimizing each network’s capacity to handle and counteract large-scale attacks. In turn, you’d get enhanced load times, global accessibility, and resilience against DDoS attacks.
I also expect enhanced detection systems powered by deep learning to be a thing. These blend a machine learning model with a knowledge graph method to improve accuracy and handle abnormalities in network performance faster than existing solutions.
When trained, the system updates itself to retain a proactive stance.
Guarding Your Online Assets With DDoS Protection
As potent cybercrime weapons go, DDoS attacks are right there at the top. They’re cheap, fairly efficient, can be automated, and in the hands of tenacious hackers, can deal crippling damage. To make matters worse, no one is safe, and everyone is a target.
That is not going to change. In fact, I’m pretty sure things are only going to get more serious as the raw power of these attacks increases. Technology evolves, and so do cyber threats.
This means you have to keep your guard up at all times. As you’ve read above for the past 15 or so minutes, it’s completely possible to protect your digital assets from DDoS attackers — you just need to make the right moves.







